This week’s lectures focused on malware defense, or in other words, how to prevent an attack from occurring in the first place. They were delivered by Craig Schmugar, another engineer at McAfee. While the lectures and labs were interesting, I think that they fell a bit short of this goal.
Perhaps I misunderstood the intent, but the lectures still focused mostly on identifying and investigating malware rather than protecting against it. Defense was only mentioned in a few parts. Anyway, onto the lectures and lab.
Methods of Attack
The lectures began with a reference to the Happy99 worm, which spread across the internet 20 years ago. According to the presenter, it was the first email worm that achieved wide distribution and infection. It affected tens of millions of people around the world. Besides spreading itself, it did no further damage.
The presenter also spoke about other methods of attack. There was not much new compared to the last two weeks of lectures. One thing that did stick out was malware that changes a configuration (like routing traffic through a proxy) and then deletes itself. It leaves no files (evidence) behind, just a modified URL in the routing table. In this sense it’s a lot like a traditional criminal. The “good” ones cover their tracks.
Proposed Solutions
So what can be done to defend against attacks? Some proposals from the lectures:
- Education: If this looks weird, too good to be true, etc., don’t click it.
- App store model: Central clearing house for good software maintained by a single entity (Apple, Google, etc.).
- Blocking: Script blockers, blocking installs, etc. Firewall as network intrusion protection. Even epoxy in USB port.
- Defense in depth: Multiple layers of defense.
This is not an exhaustive list, obviously, but it provides some ideas.
yara
Yara is a pattern matching tool for malware detection. It allows searching for strings and other parameters on a machine. A yara rule might look like this:
autorule ExampleRule
{
strings:
$my_text_string = "text here"
$my_hex_string = { E2 34 A1 C8 23 FB }
condition:
$my_text_string or $my_hex_string
}
I pulled this directly from the yara docs, which are available here.
For the labs, I used yara on a virtual machine to narrow down to a particular list of files. I was able to search via string. It’s possible to searching for other things besides strings, though, like file size, and to add in conditionals and wildcards.
Cuckoo
The other tool we explored this week was Cuckoo Sandbox (or just Cuckoo), which is an open-source program which allows automatic analysis of suspected malware. The automatic analysis part is important because of the increase in malware. Consider the following graph, which shows the number of unique malware samples (based on their hash) collected over time:
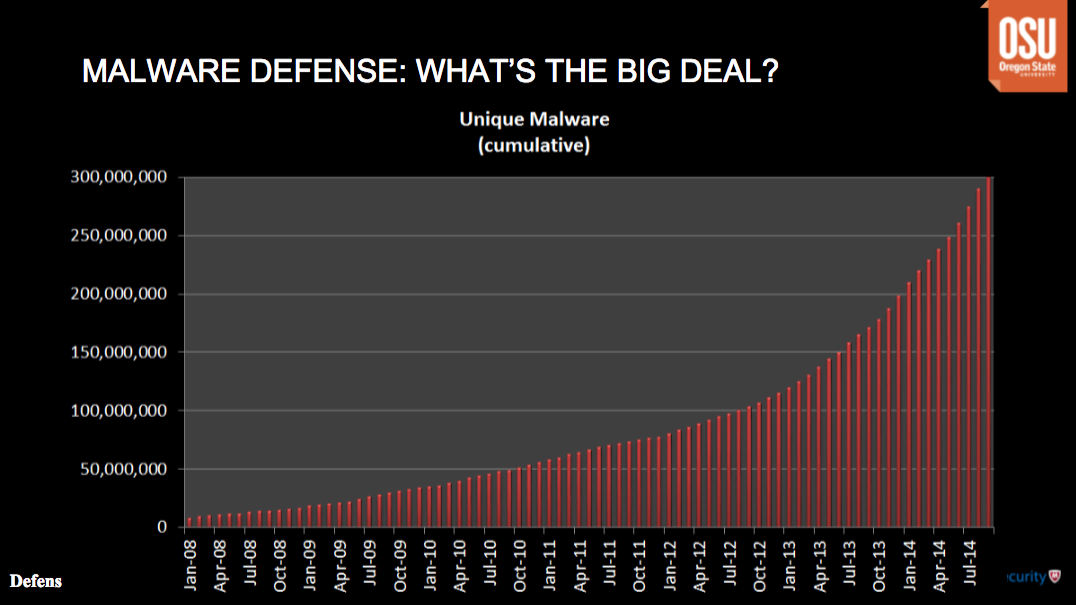 This graph is now pretty outdated, but it shows an exponential gain in the amount of malware over time.
This graph is now pretty outdated, but it shows an exponential gain in the amount of malware over time.
The presenter said that one theory for this trend is that anti-virus software is working. As such, malware creators have to keep changing their tactics and methods in order to keep up. It’s like an arms race, with each side continually upping the ante.
Anyway, back to Cuckoo. The program works by taking advantage of an isolated environment (sandbox, generally, or virtual machine more specifically) in which to run the suspected malware. The fact that the environment is isolated prevents the suspected malware from affecting or harming other parts of the machine on which it’s run. The effects of the suspected malware are then observed inside the sandbox. The fact that the process is automated is important because it speeds up malware analysis and allows more samples to be investigated in a shorter period of time.
Lab
Of the four samples that were provided, I found at least one of them to be malware: the file with the signature which begins “068D5B62254D…” According to the listing on McAfee’s website, this is a trojan designed to steal passwords.
I was able to isolate the malware using the following rule in yara:
rule FindMalware
{
strings:
$a = "MZKERNAL32.DLL"
condition:
$a
}